How Did My Email Account Get Hacked? Yahoo Gmail Hotmail AOL Comcast
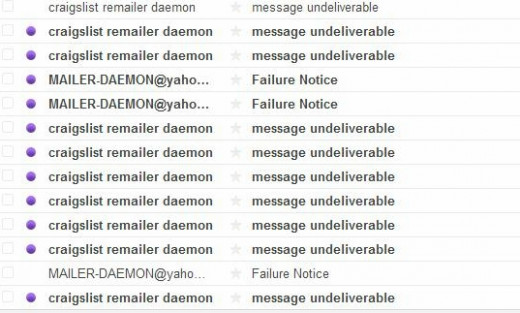
I have written a series of articles on Yahoo email Hacks, Gmail Email Hacking and Hotmail Email Break-ins. I began this series after my traumatic incident with my email account being hacked. As I wrote about before, my experience was terrible. I logged into my email account to discover an inbox filled with rebounded messages. It was very confusing at first. I never suspected I would be a victim of an email hack, but the culprit managed to find their way in… and send hundreds – to- thousands of embarrassing email spam to my friends, family, acquaintances’ and Lord knows who else. Here’s a screenshot of how my Inbox looked:
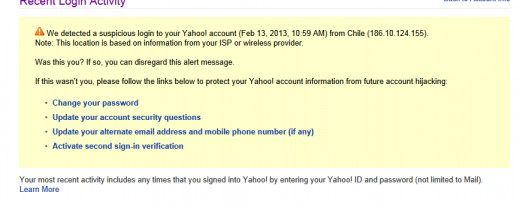
I was able to discover I was hacked when I logged into my Yahoo dashboard and saw an unauthorized user from overseas accessed my email only moments prior to the flood of rebound messages:
I then followed the directions I wrote about in my Yahoo Email Hack article to prevent future hacks, but that didn't stop me from wanting to find out HOW someone from overseas was able to access my email. So I began researching.
IS YOUR PASSWORD ON THE EASY TO HACK LIST?
In my case, I hadn't given my password out to anyone and I was able to obtain a list of the Most Common Passwords:
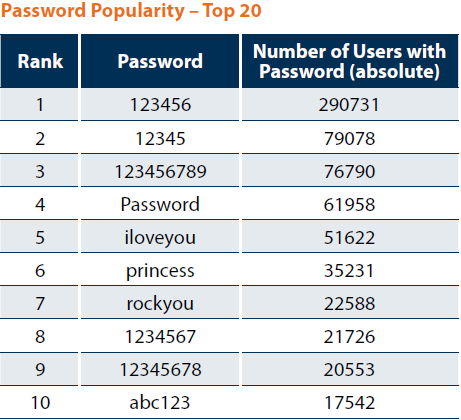
my password was not on this list, nor even close to anything on this list. So I continued to hunt.
Yahoo Email Hacks Skyrocketing For "Unknown Reasons"
According to The Next Web, Yahoo has reported giant amounts of email compromises in 2013. Yahoo does not have an explanation for the email hacks, but what is interesting about this article is that numerous people who are somewhat web-savvy have pointed out that their situation matches mine: the hack occurred without being a fault of the user. (For example, the user did not click spam links). With the quantity of people reporting they did not take actions that would cause their email to be hijacked, it appears the issue is on the Yahoo-side of the fence.
So how can one prevent a hack that is not their own fault? Some email providers, such as Yahoo, allow the user to create a Sign-in Certificate. You can also set up your email to make you enter a text message code if the IP address is suspicious. This means the user cannot enter until they get the SMS text message then enter the correct code; which is impossible unless they have access to reading your texts.
But lets say you don't use Yahoo or you aren't convinced that an "unknown problem" (on Yahoos side) is the answer...
STOP USING EMAIL LISTS
I wrote about this in my Hotmail Hack article. Many of us have friends, coworkers or acquaintances who like to send us "funny stuff" (or motivational stuff), perhaps you are one of the people that send these fun things, or perhaps you simply Forward them to your friends. But what you don't realize is that every email listed on the SEND TO is at risk of spam and and a potential hack.
So lets say your friend sends 50 people the joke email. Then each of those 50 people forward it to another 20 people; that's 1,050 email addresses that all have potential of being hacked if only ONE gets compromised.
Like I said in my other article; there's alternatives you can use if you like to send jokes or other non-important information often, such as starting a private Facebook group.
STOP CREATING FREE ACCOUNTS
Theres millions of things you can sign up for using your email address; from free cell phone apps to mailing lists for coupons to in-store promotions. The best thing to do is to create a secondary account for everything you sign up for; that way, if the secondary account gets compromised, there's no personal information in it. BE SURE TO USE A DIFFERENT PASSWORD.
INSTANT MESSENGER DANGER
If you get instant messenger / chat requests from unknown individuals, do NOT accept them nor respond to them. Hackers are able to obtain your IP address, port information and other information within seconds of you responding.
If you receive an instant messenger request from someone you believe is a friend, shoot them a quick text message or phone call to verify that they are the one who is trying to add you and NOT a hacker. In one case, my friend had his cell phone stolen. The phone allowed a local individual to access his connected email, including his instant messenger account. This individual then began contacting people through messenger and pretending to be my friend.
DOES YOUR COMPUTER HAVE A VIRUS?
It's quite possible your computer has a virus and you are unaware. You may not have done anything to get a virus. In my case, it's very possible that my computer got a virus from allowing friends to use it. While I can control what links I click and what sites I view, I cannot control what a friend does while on my pc. To refer you back to the Yahoo article written by The Next Web that states, quote:
"...attackers have apparently been referencing a non-existent MSNBC news report in the email. The bit.ly URL that is included (we’re not linking it here for obvious reasons) redirects to a fake MSNBC page that reportedly hijacks your Yahoo Mail account immediately if you are logged in."
All it takes is a friend or family member using your pc to view their email, then clicking this link.
Most Backdoor viruses go undetected until your computer goes haywire.
SAME PASSWORD USE
If you use the same password for your email account, social networking sites and other things; each time you use the same password, you run the risk of a hack. For example, if your Hotmail password is the same as your password for Facebook; should Facebook get hacked then your information is exposed.
USING FREE WIFI INTERNET CAN RESULT IN A HACK
As reported, "Man in The Middle" (Also known as MITM) attacks are simple and done right in front of you without you ever knowing. While you are kicking back at the local bistro and sipping your Caramel Latte, you log onto the Free WIFI. Meanwhile you have no idea that someone has set up their computer to act like a router. This tricks your computer into thinking that the computer actually IS the router. Then the REAL router thinks the culprits computer is your computer...but it is not... the culprits computer is "in the middle" of your computer and the real router, hence the name.
UNSUBSCRIBE LINKS
Another tricky way to get someone to click links is to annoy them with emails...with UNSUBSCRIBE links that aren't really to unsubscribe at all. So before you UNSUBSCRIBE to anything; instead use your MARK AS SPAM icon and have it sent to your trash folder. Now it will never annoy you again and you don't have to worry about clicking a dangerous link.
COULD YOUR HACK BE IN-HOUSE?
it is very important to look at all aspects of a hack situation, and the answer may not be what you were looking for. Unfortunately, anyone who has access to your computer can install a program that is called a Keylogger. (Keylogger viruses can also be installed by clicking links). A Keylogger program does exactly what the name is: it "logs" "keys", meaning, everything you type is recorded and visible to the "keylogger". Every key you type, from passwords to private emails is now recorded in a database, so-to-speak.
If you have a significant other, roommate, roommates friends or anyone that wants to read what you are typing on your PC, be very cautious.
A Keylogger program works like this:

This particular keylogger program is available for about $100.
A jealous or paranoid individual can easily place this onto your PC when you are not paying attention and "secretly" monitor all of your actions.
REMOVING A KEYLOGGER PROGRAM
Removing a Keylogger will most likely require one of the two following:
1. Having your computer reformatted
2. Finding out where the Keylogger came from and contacting them. For example, if your computers HISTORY shows visits to a suspicious site, such as WebWatcher.com, you must contact them and they will immediately deactivate the account of the user. I wanted to see how they operated, so here's my correspondence with LIVE CHAT:
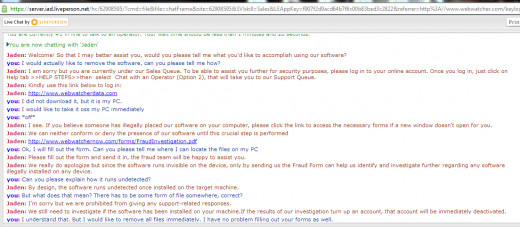
IN LARGER PRINT: MY COMMUNICATIONS WITH KEYLOGGER SUPPORT
You are now chatting with 'Jaden'
Jaden: Welcome! So that I may better assist you, would you please tell me what you'd like to accomplish using our software?
you: I would actually like to remove the software, can you please tell me how?
Jaden: I am sorry but you are currently under our Sales Queue. To be able to assist you further for security purposes, please log in to your online account. Once you log in, just click on Help tab >>HELP STEPS>>then select Chat with an Operator (Option 2), that will take you to our Support Queue.
Jaden: Kindly use this link below to log in:
Jaden: http://www.webwatcherdata.com
you: I did not download it, but it is my PC.
you: I would like to take it oss my PC immediately
you: *off*
Jaden: I see. If you believe someone has illegally placed our software on your computer, please click the link to access the necessary forms if a new window doesn't open for you.
Jaden: We can neither conform or deny the presence of our software until this crucial step is performed
Jaden: http://www.webwatchernow.com/forms/FraudInvestigation.pdf
you: Ok, I will fill out the form. Can you please tell me where I can locate the files on my PC
Jaden: Please fill out the form and send it in, the fraud team will be happy to assist you.
Jaden: We really do apologize but since the software runs invisible on the device, only by sending us the Fraud Form can help us identify and investigate further regarding any software illegally installed on any device.
you: Can you please explain how it runs undetected?
Jaden: By design, the software runs undetected once installed on the target machine.
you: But what does that mean? There has to be some form of file somewhere, correct?
Jaden: I'm sorry but we are prohibited from giving any support-related responses.
Jaden: We still need to investigate if the software has been installed on your machine.If the results of our investigation turn up an account, that account will be immediately deactivated.
you: I understand that. But I would like to remove all files immediately. I have no problem filling out your forms as well.
Jaden: You can reformat your machine that will remove all the programs illegally placed on your computer including WebWatcher.
you: I already contacted the local PC place, that was also their suggestion, but that requires me to pay $200 and potentially lose data.
- - - - - - - - - - - - - - - - - - - - - - - - - - - -
And that's where my conversation ended because I could tell I was getting nowhere.
Then I discovered that Keyloggers do not need to come in the form of programs. Check out the keyloggers below, available for sale on Amazon.com:
NEXT: READ MY FOLLOW-UP ARTICLE
Next please read WHAT TO DO AFTER YOUR EMAIL HAS BEEN HACK AND SPAM SENT. This article will explain practical ways to help you get over the embarrassment of your current situation.
SO... NOW WHAT?
Hopefully this article has added some insight as to who could have hacked your email and how you can prevent future hacks. Check out my other articles on this topic and be sure to take my poll below:
HAS YOUR EMAIL BEEN HACKED?
- How to File a Legal Case Against a Stalker / Harasse...
Everything you need to know about Stalking, Harassment, PPO's, Restraining Orders, Criminal and Civil Cases. A must-read before going to police or contacting a lawyer. - Truth About SMALL CLAIMS COURT: How to File Case and...
Everything you need to know about the Small Claims Court Legal Process from start to finish. Before you take action, be sure to read this article. Small Claims Case Myths Exposed. - The Difference Between a PPO and a Restraining Order
If you are involved in harassment, stalking, cyber-stalking, cyber-bullying or need protection from someone, learn the difference between a Personal Protection Order and a Restraining Order - Am I Being Stalked: Signs of Stalking Harassment
Do you feel like someone is Stalking you online or in-person? Learn signs of Stalking and Harassment. Stalking is NOT legal and you do not have to tolerate it! How to protect yourself from Stalkers. - How to Report Internet Spam, Unwanted Calls, YouTube...
In my last article, I uncovered a new Domain Renewal Scam/ Spam. in today's article I will teach you exactly how to report Internet Spam, Scams and Harassment from them. - How to Stop and Report Youtube Harassment Stalking
Cyberbulling isn't just related to teens. From co-workers to employees to relationships-gone-south; internet harassment comes in many forms, including YouTube. Learn how to Report and Stop it today! - How to Stop and Report Facebook Harassment Stalking
Cyber Bullying is everywhere; from Google Voice to Twitter to Facebook - learn how to identify Facebook harassment and report it. Harassment is not legal and you do not have to take it! - How to Stop and Report Facebook Harassment Stalking
Cyber Bullying is everywhere; from Google Voice to Twitter to Facebook - learn how to identify Facebook harassment and report it. Harassment is not legal and you do not have to take it! - CHASE Bank Account Hacked: Banking Fraud
It happens when you least expect it - a sudden withdrawal or charge that you have no knowledge of. It can quickly become the scariest moment of your life - OR it could all be a scam. READ THIS FIRST! - How to Deal With An Email Hack and Spam Sent
Maybe you have read my prior articles about how absolutely awful an email - What to Do if Yahoo Email Has Been Hacked
How to tell if your email has been